Original article from: 8 November – 2014.
It still gives good tips on what I went through when the site was hacked.
My site was hacked
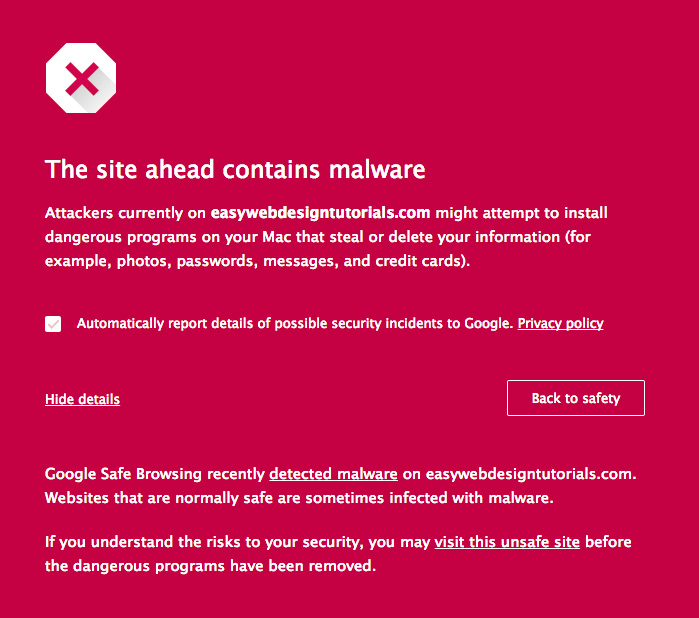
My site Easy Web Design Tutorials was hacked through one of my other sites at Bluehost and the infection spread.
In June Bluehost e-mailed me that one of my sites had malicious files detected and had then also removed these. It was awesome to see that Bluehost were active in removing malware.
Fast forward to….
Mid-September.
The WordFence security WordPress plugin alerted me well ahead of time of JS files that had been infected, but I did not know what to do about it. So I e-mailed them asking for advice.
I installed the Anti-Malware and Brute-Force Security WordPress plugin by ELI. Ran the site scan, but it did not find any errors or problems.
I also checked the site at https://sitecheck.sucuri.net/ and no errors were found.
I thought that WordFence was playing tricks with me and giving me what is called a false positive (a false warning), but obviously when I look at it now it had not done so.
A week passed and I had e-mailed the author of WordFence asking what to do with the long list of infected JS files. They told me to send some samples which I did (but these were not infected even though it said that they were). I also gave access to the site so they could check.
I e-mailed Bluehost asking if they could check my site. No response.
A response came from Mark the developer of WordFence telling me to work with my hosting provider to fix the problem. He told me that the files had been modified by a hacker to inject malicious code.
End of September.
The infection had spread. Even Google now had placed the “The site ahead contains malware” onto my site. Easy Web Design Tutorials was shut down in Chrome, but Firefox, Opera etc my site was still online.
Since I was working on a version 2 of this site I deleted the online site, and uploaded the new site. Checked my site at Sucuri once again and it was clean…. for an hour. The infection had also crossed into the new site.
I scanned and cleaned the site with the Anti-Malware plugin from Eli and it worked. The site was clean again….for an hour. It was obviously an deeper issue going on.
I e-mailed Bluehost again and once again they did not respond (they responded 5-6 days later).
I then facebook messaged one of the guys working at Bluehost. He advised me to use their Site Doctor $50 cleanup service. The service would clean up the full cPanel account. It seemed like that was just what I needed so I decided to go ahead with their service. The Site Doctor service really cleaned up all my sites and the cPanel account. I checked the site at Sucuri again and it was clean, and is still clean. Thanks to the Site Doctor I got my site cleaned up. BUT I could have avoided so much trouble if Bluehost had responded to my e-mails. Then again I went through an interesting learning experience along the way because Bluehost did not respond. So everything has its place. I just got to say…. normally Bluehost is pretty good at responding to my e-mails.
What I learned from this experience.
Install WordFence on all my sites or check out Ninjafirewall. IF a scan comes up and something is wrong. Install the Anti-Malware plugin to clean it up. (WordFence and the Anti-Malware plugin really should merge.)
Then check the site at Sucuri site check.
I have also begun to install iThemes Security plugin on a few of my sites. As it has a lot of functions to tighten the security of a site.
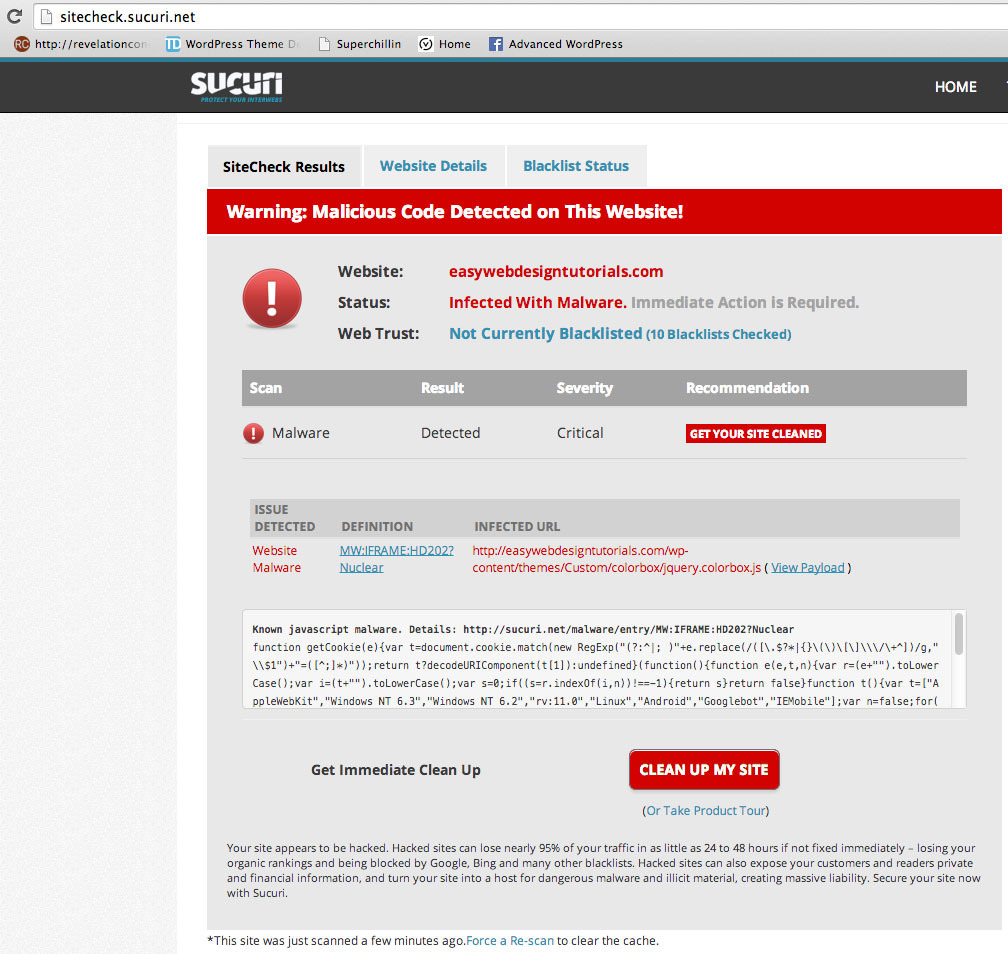
Here is what is looked like one of the times I checked the site at https://sitecheck.sucuri.net/
(other times I had a long list of infected files)
I also changed my various passwords and made them stronger.
Check my Security article for additional information. The article will be added onto the more information that I come across.
Resources:
blokt.com/guides/what-is-spyware